Better Fraud Data. Better Defense.
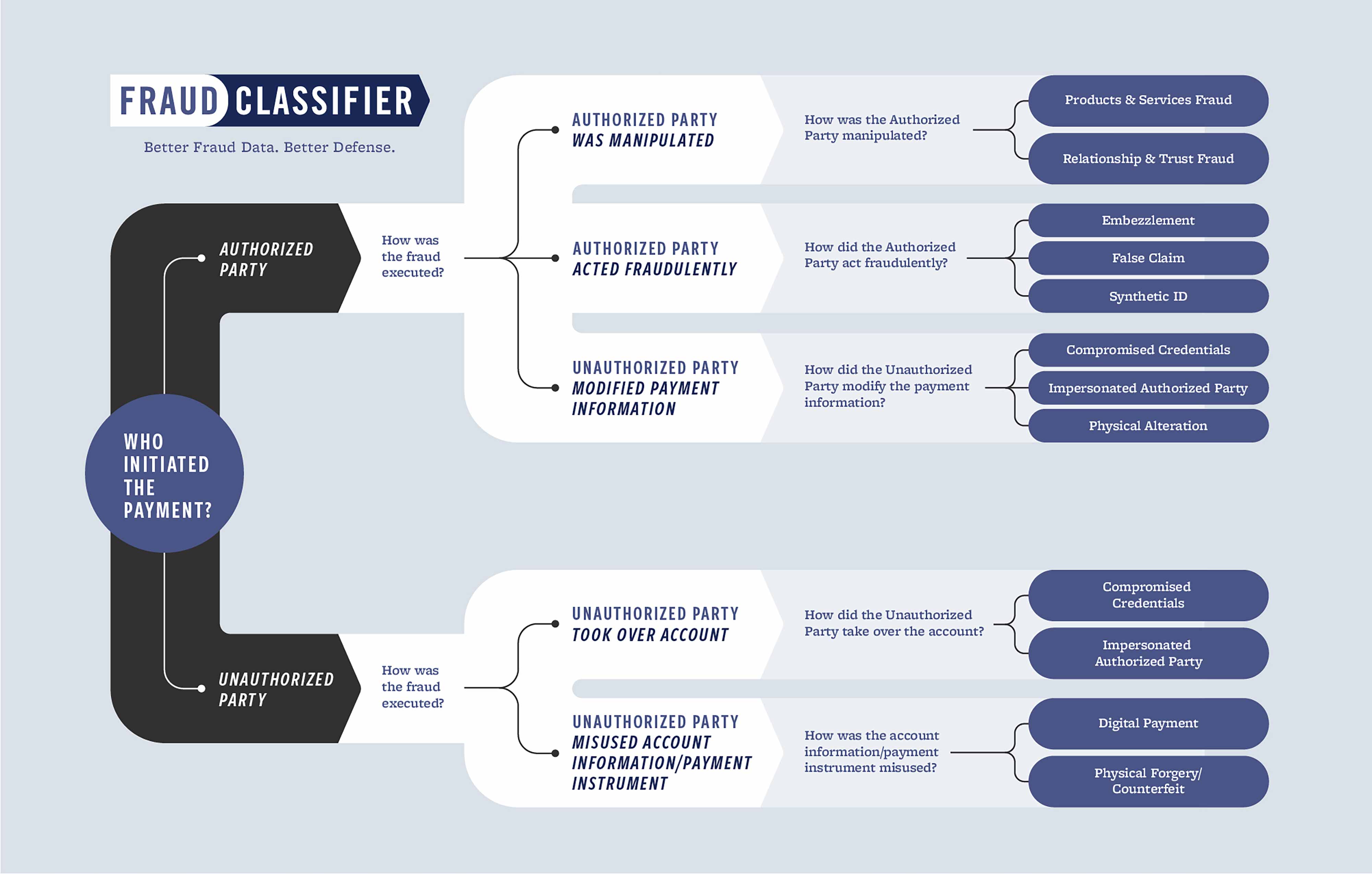
The FraudClassifier℠ model provides an intuitive approach to classifying fraud involving payments. It enables payments stakeholders to classify fraud independently of payment type, payment channel or other payment characteristics. The model includes supporting definitions to facilitate consistent application across the industry.
This interactive experience provides the ability to navigate through different fraud classification paths within the model and view a fraud scenario that relates to that particular classification path. Once you've navigated through one path, there is an option to start over and try a new path!
Tip: Click the "?" next to each question for more information and to view the supporting definitions.
Classification Path
View the classification path display as you navigate through each question.
Fraud Classification
Authorized Party Was Manipulated - Products & Services Fraud
Scenario
In addition to his recurring condo fee payments, Paul received an invoice for planned roofing repairs that appeared to be from his condo association. Paul sent a check to the address on the invoice. Soon after, he reached out to the condo association only to be told that the roof had just been replaced a couple of years ago and they had never sent an invoice.
Explanation
Paul paid the invoice with his money (or from his account). He did so believing he was paying for a roof repair to his condo when in actuality, no roof repair was conducted and the invoice he received was fake/fraudulent.
Fraud Classification
Authorized Party Was Manipulated - Relationship & Trust Fraud
Scenario
Joan fell in love with Fred via an online dating site. They decided to meet in person. A day before meeting, Fred asked Joan to wire him $10,000 to get out of serious trouble. Joan wired the money to Fred. The next day, Fred did not show up for their date as planned. Joan made several attempts to reach out to Fred but never heard from him again.
Explanation
Joan gave Fred money from her account. She was manipulated by Fred to send the money via Fred's guise of beginning a romantic relationship.
Fraud Classification
Authorized Party Acted Fraudulently - Embezzlement
Scenario
Tina, the company treasurer, had the ability to initiate ACH payments at her company. Tina decided to initiate and authorize a large ACH payment from her company's account to an outside account under her control. She then withdrew those funds to settle her personal financial debts.
Explanation
As the company treasurer, Tina is authorized to initiate ACH payments at her company (for business purposes, within the company guidelines). However, she chose to abuse her access to initiate payments and direct company funds into her own account to use for personal reasons.
Fraud Classification
Authorized Party Acted Fraudulently - False Claim
Scenario
Betsy used a computer at the town library to order new merchandise online, making the payment with an electronic check. Days after she received the goods, she called her bank and reported the purchases as fraudulent. Betsy stated that she did not place the order or make the payment, and suggested her account information or credentials must have been stolen and misused.
Explanation
Betsy purchased merchandise with her money and received that merchandise. She then intentionally defrauded the bank by claiming she never made that purchase (and lying about the whole situation).
Fraud Classification
Authorized Party Acted Fraudulently - Synthetic ID
Scenario
Fred opened a deposit account under a fabricated identity that included both stolen information as well as made up information. After a large deposit into that account, Fred initiated a wire transfer to an offshore account. He never transacted on the fabricated identity account again.
Explanation
While Fred opened an account with a fabricated identity, he is an authorized user on that account. He committed fraud in order to open the account (and therefore acted fraudulently), and did so via creating a synthetic identity.
Fraud Classification
Unauthorized Party Modified Payment Information - Compromised Credentials
Scenario
Steve setup an online recurring bill payment from his bank account while his roommate was nearby. His roommate later authenticated into Steve's account using Steve's ID/password and modified the recurring payment. Upon processing of the payment, funds were redirected to an account under the roommate's control.
Explanation
According to the definition of payment initiation, Steve is the one who initiated the payment, being an authorized party as he legitimately set up the online payment from his own bank account. This payment initiation was then modified by his roommate (an unauthorized party). The roommate was able to modify the payment because he had Steve's ID and password, or rather, Steve's credentials had been compromised.
Fraud Classification
Unauthorized Party Modified Payment Information - Impersonated Authorized Party
Scenario
Jim scheduled an online bill payment using his own bank account information. A day later, Jake represented himself as Jim by successfully answering verification questions asked by the call center associate. Jake (as Jim) then instructed the call center associate to modify the scheduled payment, redirecting it to an account in his control. Upon receipt of the payment, Jake withdrew the funds.
Explanation
According to the definition of payment initiation, Jim is the one who initiated the payment, being an authorized party as he legitimately set up the online payment from his own bank account. This payment initiation was then modified by Jake, an unauthorized party. Jake was able to modify the payment by impersonating Jim when he called in, not having Jim's credentials, but having enough information to make the call center associate believe that Jake was, in fact, Jim.
Fraud Classification
Unauthorized Party Modified Payment Information - Physical Alteration
Scenario
Susan hired a concierge service. Pauline showed up, indicating she worked for the concierge service. Susan asked her to buy her an item at the store, and gave her a signed check from her own checkbook to cover the cost of the item. Pauline then changed the payee and amount information on the check, and deposited it to her own account.
Explanation
The signed check represents an initiated payment, which was initiated by Susan. Susan owned the account reflected on the check she signed and was, therefore, an authorized party. Pauline then physically modified the check, which she did not have the authority to do so, being an unauthorized party.
Fraud Classification
Unauthorized Party Took Over Account - Compromised Credentials
Scenario
Using Greg's login ID and password, Frank gained full access to Greg's online bank account. Frank then proceeded to initiate several wire transfers from Greg's account to a different account under his control. Once Frank drained Greg's account, he changed the login password and logged out.
Explanation
Frank initiated wires from Greg's account. Frank did not own the account nor did he have permission to use Greg's account. Frank obtained Greg's credentials (his ID and password), which enabled Frank to gain control of Greg's account, resulting in an account takeover.
Fraud Classification
Unauthorized Party Took Over Account - Impersonated Authorized Party
Scenario
Through a call center, Frank represented himself as Greg Jones using Greg's stolen personally identifiable information. Frank then requested a large wire transfer to an account under his control, and instructed the call center associate to close his (Greg's) now empty account.
Explanation
The payment was initiated out of Greg's account, but was called in by Frank, an unauthorized party. Frank was able to convince the call center he was Greg, having Greg's personally identifiable information in his possession. Frank then closed Greg's account, assuming full control of the account and blocking Frank from any further action on his account.
Fraud Classification
Unauthorized Party Misused Account Information/Payment Instrument - Digital Payment
Scenario
Carl found an old check from Frank. Using the account information from the check, Carl initiated an online payment on the university's website to cover the cost of his fall semester tuition bill.
Explanation
The check belonged to Frank and had Frank's bank account information on it. Carl then used Frank's bank account information (from the check) to initiate a payment to his benefit. Carl did not have enough information to take over Frank's account, but did have enough information to initiate a payment.
Fraud Classification
Unauthorized Party Misused Account Information/Payment Instrument - Physical Forgery/Counterfeit
Scenario
Dan, who works in the mailroom, stole blank corporate checks from the office. He wrote the checks to himself, forged the signature as an authorized representative of his company, and then cashed all of them.
Explanation
Working in the mailroom, Dan is clearly not in any type of accounts payable role at his company and therefore, does not have the authority to sign the company checks he found. While he does not have complete control of the company's payment account, he had enough information to initiate a payment and did so through the physical forgery of the blank checks.
Stay Engaged
Receive updates and learn more about the FraudClassifier model.
Share
The FraudClassifier Model
Copyright © 2026 Federal Reserve Banks. All rights reserved.
The FraudClassifier model was developed by a cross-industry work group to provide a consistent way to classify and understand how fraud occurs across the payments industry. The FraudClassifier model is not intended to result in mandates or regulations, and does not give any legal status, rights, or responsibilities, nor is it intended to define or imply liabilities for fraud loss or create legal definitions, regulatory, or reporting requirements. While sharing and use of the FraudClassifier model throughout the industry is encouraged, any adoption of the FraudClassifier model is voluntary at the discretion of each individual entity. Absent written consent, the FraudClassifier model may not be used in a manner that suggests the Federal Reserve endorses a third party product or service.
