Stay Vigilant to Avoid Scams
Paying attention to tactics used by criminals to commit fraud can be challenging, especially when one is under emotional pressure to make a quick decision. However, advance awareness of scam tactics can help individuals and businesses avoid the detrimental consequences of scams, such as financial losses and the associated emotional toll.
For an overview of the different types of tactics criminals use to commit scams, watch this video below.
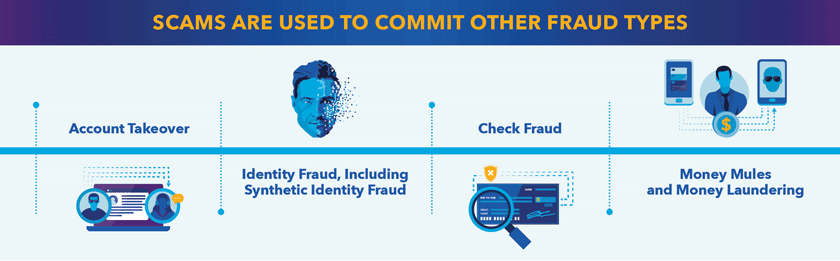
Another common tactic for criminals is to use scams as an entry point to commit other types of payments fraud, such as check fraud and account takeovers.
Increased knowledge of scams — how they work and the potential impacts — can help individuals and businesses identify scams and take steps to avoid them.
Test Your Knowledge: Can You Spot the Scam?
Individuals and businesses can prevent falling victim to scams if they look for various red flags — but some warning signs are more obvious than others. Test your ability to detect scams by reviewing three scenarios.
Downloadable Resources
Explore these resources for additional information on scam tactics and impacts.
| Document Title | Format | Reading Time |
|---|---|---|
| Scam Tactics (PDF) | Document | 4 minutes |
| Romance Impostor Scams: How Criminals Exploit Trust to Steal Money (PDF) | Document | 5 minutes |
| Scam Impacts: Betrayal and Damage (PDF) | Document | 3 minutes |
| Beyond a Scam: Connections to Other Types of Payments Fraud (PDF) | Document | 5 minutes |
| Supercharging Scams: How Criminals Use Modern Technology to Deceive and Manipulate Their Victims (PDF) | Document | 5 minutes |
| Leveraging the ScamClassifierSM Model for Check Scams (PDF) | Document | 4 minutes |
| Addressing Deposit Fraud Using Both the ScamClassifierSM and FraudClassifierSM Models (PDF) | Document | 5 minutes |
| Romance Scams, Check Fraud and the ScamClassifierSM Model (PDF) | Document | 4 minutes |
| Malware Security Alert Email (PDF) | Document | 3 minutes |
| Unpaid Toll Text Message (PDF) | Document | 2 minutes |
| Job/Employment Scam (PDF) | Document | 2 minutes |
| Cryptocurrency Investment Scam (PDF) | Document | 2 minutes |
| Your Payment Was Received Email - And It's Not a Scam (PDF) | Document | 2 minutes |
The scams mitigation toolkit was developed by the Federal Reserve to help educate the industry about scams and outline potential ways to help detect and mitigate this fraud type. Insights for this toolkit were provided through interviews with industry experts, publicly available research, and team member expertise. This toolkit is not intended to result in any regulatory or reporting requirements, imply any liabilities for fraud loss, or confer any legal status, legal definitions, or legal rights or responsibilities. While use of this toolkit throughout the industry is encouraged, utilization of the toolkit is voluntary at the discretion of each individual entity. Absent written consent, this toolkit may not be used in a manner that suggests the Federal Reserve endorses a third-party product or service.

