Business email compromise (BEC) is a leading cause of fraudulent ACH and wire transfers from business deposit accounts — accounting for 73% of all reported cyber incidents in 2024 (Off-site), a sharp increase from 44% in 2023. BEC strategies generally are straightforward: criminals send an email message that appears to come from a known sender (Off-site) making what seems to be a legitimate payment request. According to a 2025 report, 79% of organizations were victims of payments fraud attacks and attempts in 2024. Top BEC tactics (Off-site) were third-party impersonation (63%), vendor impersonation (60%) and senior executive impersonation (49%).
The FBI reports that business email compromise has become a $55 billion scam (Off-site) over a 10-year time frame
Today’s BEC threats are more complex and dynamic than in the past — in part, due to more easily accessible data about victims and increasingly sophisticated schemes, such as deepfakes created with generative artificial intelligence (AI) that impersonate legitimate people.
Criminals can readily find information about authorized individuals who have access to initiate an ACH or wire transfer within business banking platforms. They may use BEC to siphon funds out of business accounts by:
- Deceiving or manipulating authorized users into sending funds
- Pretending to be the authorized user on a business account
- Attempting to be added as an authorized party to a business account or to the business’ banking platform
Business email compromise evolves constantly, complicating fraud mitigation efforts. Using a classification structure, such as the FraudClassifierSM model, can help users consistently identify how the fraud occurred, such as by modifying existing payment information, taking over the account or manipulating an authorized party. Furthermore, using the model can uncover what facilitated the BEC, such as compromised credentials, impersonation of authorized parties, or relationship and trust scams — as identified by the blue arrows below.
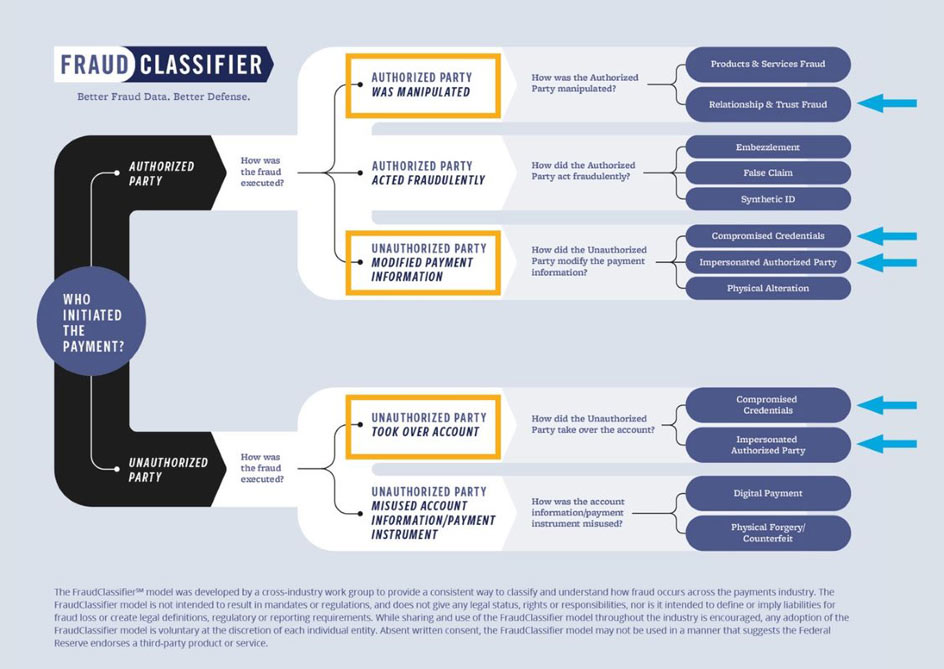
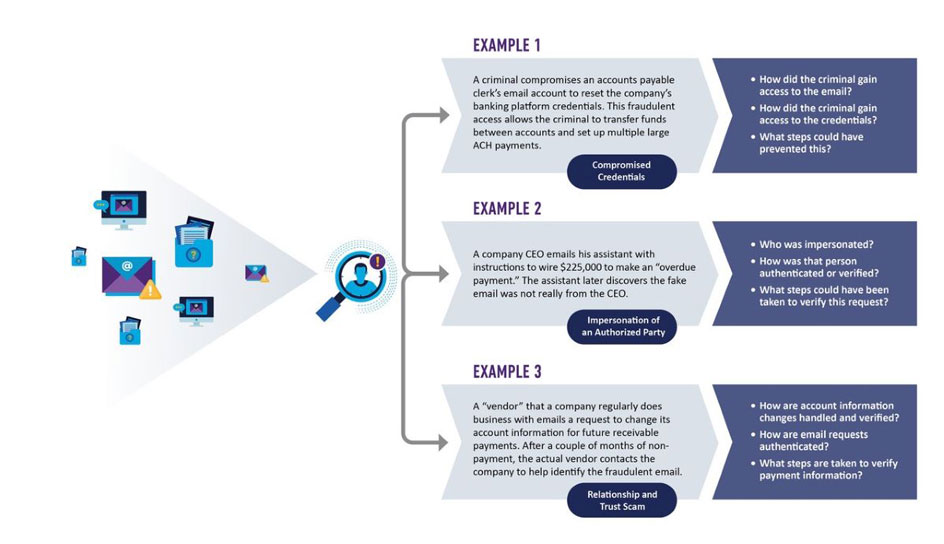
This level of classification can be used to identify the root cause of the fraudulent occurrence through a series of questions as shown below. This analysis may highlight opportunities to strengthen processes, training and education. While the examples below focus on ACH and wire transfers, the questions can be used to analyze any payment type.
 Understanding vulnerabilities can encourage financial institutions and their business customers to take steps to reduce their risk, such as:
Understanding vulnerabilities can encourage financial institutions and their business customers to take steps to reduce their risk, such as:
- Multi-factor authentication (MFA). MFA relies on two or more variations of something you have, something you know and something you are.
- Dual verification. Transaction requests and changes can require a secondary review and approval before they can be processed. This creates a pause (which offers time to identify and circumvent the BEC) and an added layer of verification.
- Dynamic passwords. Passwords that change frequently, such as those used during two-factor authentication, can offer a more secure authentication method than static passwords.
- Code words. Also known as security words or phrases, these are determined in advance of transaction requests and are used to verify that requests are truly from authorized people and not someone attempting to impersonate them.
- Enhanced employee training. Education about BEC can help staff members at financial institutions and businesses recognize the signs of potential fraud and equip them with knowledge about how best to handle suspicious requests. Consider training employees on a recurrent basis about phishing (fraudulent communications that appear to come from legitimate sources) and other social engineering tactics to keep it top of mind.
- ACH blocks and Positive Pay. These fraud mitigation tools can be set up by a financial institution, allowing a business to manage its debits and credits by requiring review of transactions that have not been pre-approved or that meet pre-defined transaction requirements.
- Authorized user set-up and regular review. Using a secure process to set up new access to a business account, as well as regularly reviewing users who have access, can reduce the risk of unauthorized changes and transactions. Other considerations also may include limiting risk by setting dollar limits, date/time accessibility and other restrictions.
Staying aware of BEC tactics and proactively planning for the BEC variations criminals use can help protect financial accounts from BEC risks and deter the continued growth of ACH and wire transfer fraud.
Stay Connected
Keep informed about the Fed’s efforts to support payment security and mitigate fraud by joining the FedPayments Improvement Community.
Sharing and use of the FraudClassifier model throughout the industry is encouraged; any adoption is voluntary. The FraudClassifier model is not intended to result in mandates or regulations, and does not confer any legal status, rights or responsibilities, nor is the model intended to define or imply liabilities for fraud loss or create reporting requirements. Absent written consent, the FraudClassifier model may not be used in a manner that suggests the Federal Reserve endorses a third-party product or service.
