Individuals can be tricked into depositing fraudulent checks. Alternatively, they may be deceived or manipulated into providing their online banking credentials to a fraudster, which allows the criminal unauthorized access to their accounts. This could facilitate fraudulent check deposits made through online or mobile banking. If customers are deceived into believing the deposit is from a legitimate source, they may spend the funds and find themselves with a financial loss when the deposited check is identified as fraudulent and removed from their account.
The Federal Trade Commission (FTC) reported consumers lost more than $12.5 billion to fraud and scams in 2024 – an increase of 25% from 2023 – despite a similar number of reports in each year (2.6 million).
Scams can lead to authorized transactions made by the authorized account owner, or unauthorized transactions, where a payment is initiated by a third party who has no legitimate right to move the money. The following scheme demonstrates how the ScamClassifierSM model can be used alongside the FraudClassifierSM model to classify an event when the root cause of unauthorized activity was a scam. Together, the models can be used to enable more robust classification for fraud reporting, prevention and education.
This article is part of a series focusing on ways to improve fraud mitigation and education by classifying check fraud and scams.
Unauthorized Deposit Fraud Stemming from a Scam
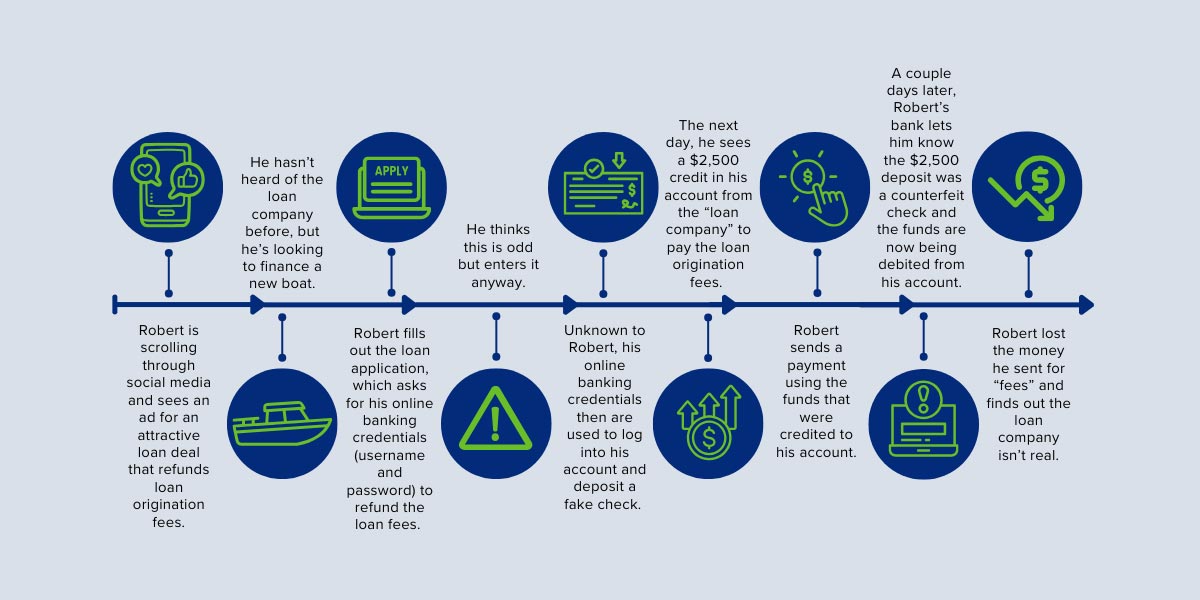
In this scenario, an individual completes a loan application believed to be directed to a legitimate lender but that is actually triggered by a criminal impersonating a lender. The application prompts applicants for their online banking credentials, which they enter and therefore, unknowingly provide a criminal with access to their online banking accounts. As a result, a fraudulent deposit is made, and the “lender” tricks the applicant into sending them funds. This scenario discusses how unauthorized deposits can originate from scams if the authorized party is deceived or manipulated into providing account access that leads to activity the authorized account holder did not initiate or approve.
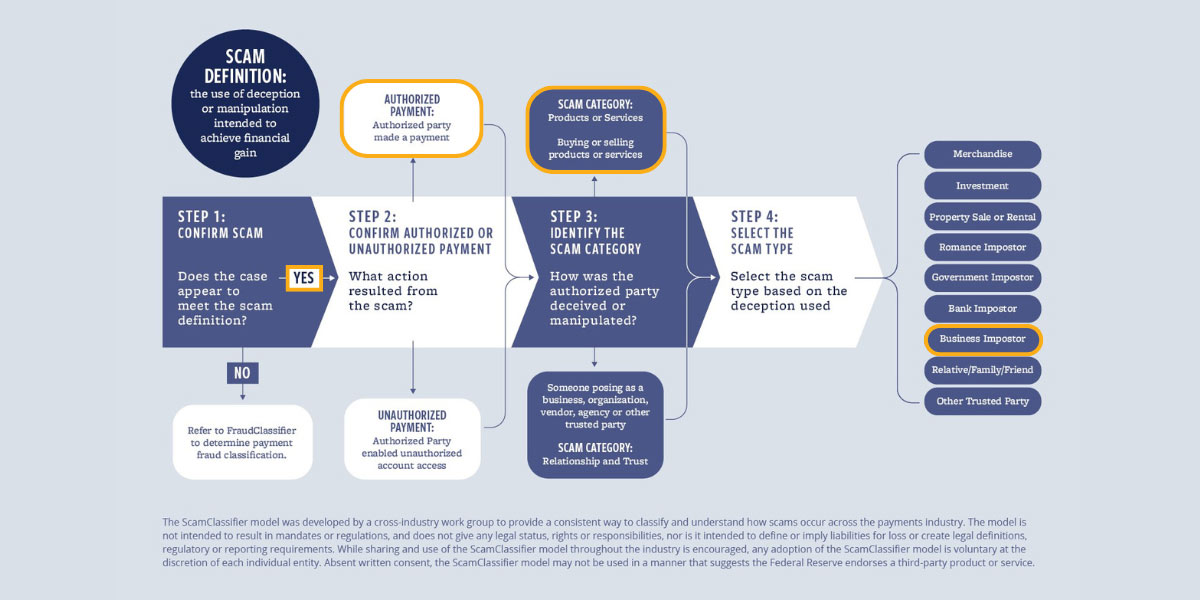
Scam > Authorized Party > Products or Services > Business Imposter
The ScamClassifier model can be used to classify the root cause of an event when it is a scam.
- Step 1 is to confirm it is a scam using the definition in the graphic below. The root cause of this case is a scam because Robert was deceived into submitting a loan application and sending money for loan fees he thought were legitimate.
- In step 2, this is considered an authorized transaction since Robert initiated the fee payment.
- Step 3 is where the scam is categorized as products or services because the loan is considered a service.
- In the final step, since the loan ad and application impersonated a lending company that Bob thought was legitimate, the scam type is “business imposter.”
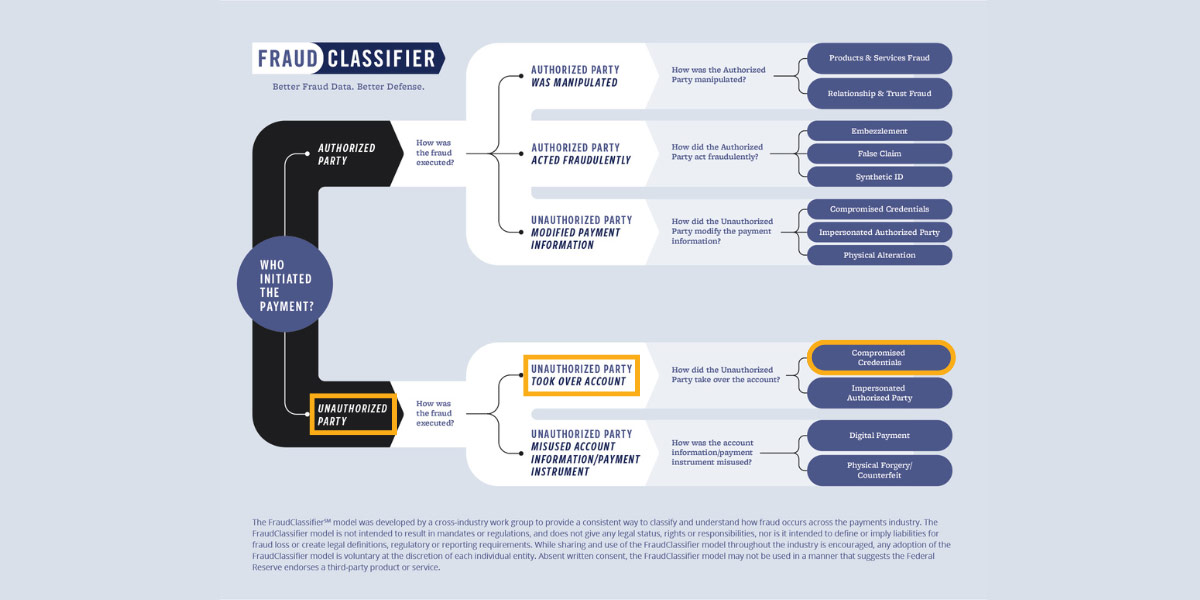
Since Robert did not initiate or authorize the $2,500 check deposit into his account, the FraudClassifier model also can be used to classify the fraud event. This additional level of classification generates more robust reporting and awareness about the root cause of the check fraud, which can be incorporated into fraud prevention strategies and education.
Unauthorized Party > Unauthorized Party Took Over the Account > Compromised Credentials
- In step 1, when determining who authorized the payment, unauthorized party is selected.
- Step 2 is where it is determined how the fraud was executed. In this case, a third party made the unauthorized deposit by taking over the account.
- In step 3, the account was taken over because the online banking credentials were compromised during the scam. The fraud classification is “compromised credentials.”
The ScamClassifier and FraudClassifier models can provide actionable insight into the trends and the corresponding root causes that are most impactful to the payment industry.
This article is part of a series on check fraud and scams, highlighting better ways to identify and classify cases using the ScamClassifier model and FraudClassifier model. Read these articles, Leveraging the ScamClassifier Model for Check Scams and Romance Scams: Another Look at Check Fraud Using the ScamClassifier Model for an examination of other common check fraud and scam scenarios with model application.
The ScamClassifier model is not intended to result in mandates or regulations, and does not give any legal status, rights or responsibilities, nor is it intended to define or imply liabilities for loss or create legal definitions, regulatory or reporting requirements. While sharing and use of the ScamClassifier model throughout the industry is encouraged, any adoption of the ScamClassifier model is voluntary at the discretion of each individual entity. Absent written consent, the ScamClassifier model may not be used in a manner that suggests the Federal Reserve endorses a third-party product or service.
Sharing and use of the FraudClassifier model throughout the industry is encouraged; any adoption of the FraudClassifier model is voluntary at the discretion of each individual entity. The FraudClassifier model is not intended to result in mandates or regulations, and does not give any legal status, rights or responsibilities, nor is the FraudClassifier model intended to define or imply liabilities for fraud loss or create legal definitions, regulatory or reporting requirements. Absent written consent, the FraudClassifier model may not be used in a manner that suggests the Federal Reserve endorses a third-party product or service.
Both “ScamClassifier” and “FraudClassifier” are service marks of the Federal Reserve Banks. A list of marks related to financial services products that are offered to financial institutions by the Federal Reserve Banks is available at FRBservices.org.
