Over the years, fraudsters often have leveraged fraudulent paper checks to help perpetrate scams – defined as the use of deception or manipulation intended to achieve financial gain. Longstanding trust in the legitimacy of paper checks, as well as lengthy processing times, can make them a lucrative target for scams and fraud. For example, a financial institution may allow a customer to access funds from a check deposit within two business days, even though it may take a week or more for the institution to be notified the check is fraudulent. The customer then loses any money that he spent using fraudulent deposit funds after they are removed from his account.
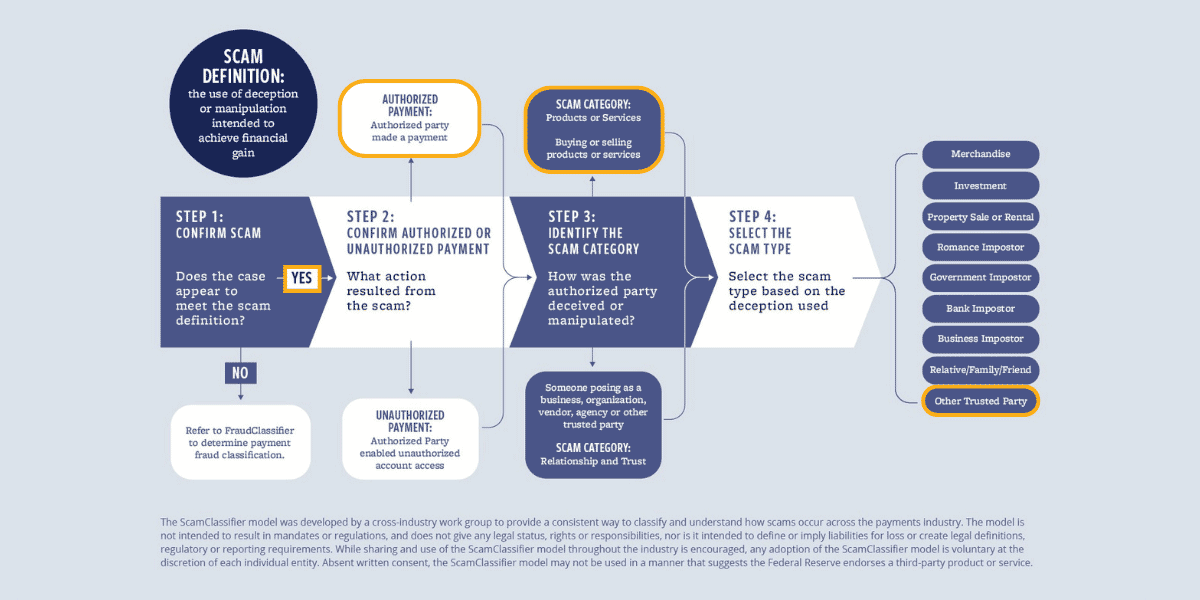
Introduced by the Federal Reserve in 2024, the ScamClassifierSM model can assist in identifying the root cause of the fraud that occurred due to a scam – either as a products or services scam, or as a relationship and trust scam. Use of the ScamClassifier model to support more consistent and detailed classification of scams can help prevent losses. In addition, having clear insights into the most relevant trends ultimately can lead to more targeted education and prevention strategies.
This article is part of a series focusing on ways to improve fraud mitigation and education by classifying check fraud and scams.
Check Fraud Scheme: The Wedding Planner
In this example, a freelance wedding planner is manipulated by a criminal. The supposed “client” sends her a fraudulent check in the mail as an initial payment for her services. The wedding planner deposits the check into her account without realizing the check is fake. Several days later, her financial institution is notified that the deposited check was created fraudulently using a stolen account number and in turn, notifies the wedding planner and removes the funds from her account.
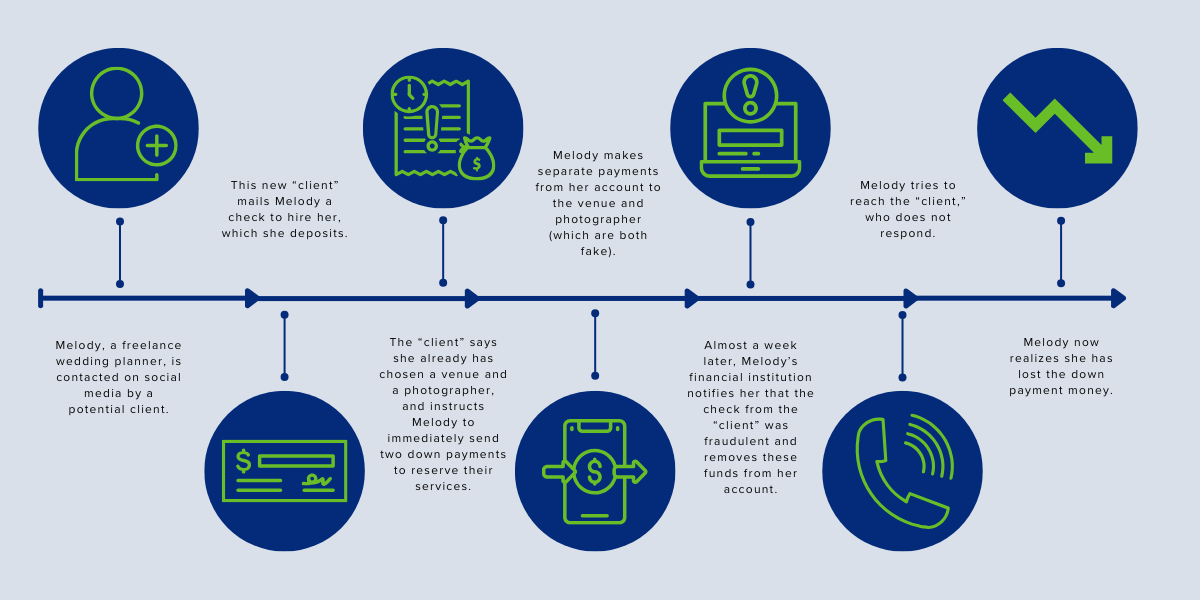
Scam > Authorized Party > Products or Services > Other Trusted Party
When this scenario is analyzed using the ScamClassifier model:
- Step 1 is to confirm it is a scam using the scam definition outlined above and in the graphic below. This case is a scam because the fraudster uses manipulation to achieve financial gain (the down payment money).
- In step 2, whether the payment was authorized or unauthorized is assessed. These were authorized payments since Melody, the authorized party, deposited the check and sent down payments to the fake venue and photographer.
- Step 3 is where the scam is categorized as products or services, because it involves Melody’s wedding planning services.
- Last, in step 4, selection of the scam type is made based on the deception used. In this case, the scam involved an “other trusted party,” signifying that many small business owners inherently trust their clients.
A key to mitigating fraud and spreading awareness about it is having a better understanding of the risk. The layers of classification within the ScamClassifier model, along with other attributes if desired, may provide a holistic picture of scams involving check fraud and corresponding trends, as illustrated by the check fraud scheme described in this article. Ultimately, greater adoption of the model also may provide more consistent industrywide classifications to facilitate sharing information between entities, assist users to identify cross-industry scam trends, and more accurately define the true magnitude of this growing problem.
The ScamClassifier model is not intended to result in mandates or regulations, and does not give any legal status, rights or responsibilities, nor is it intended to define or imply liabilities for loss or create legal definitions, regulatory or reporting requirements. While sharing and use of the ScamClassifier model throughout the industry is encouraged, any adoption of the ScamClassifier model is voluntary at the discretion of each individual entity. Absent written consent, the ScamClassifier model may not be used in a manner that suggests the Federal Reserve endorses a third-party product or service.
